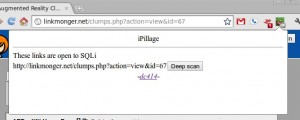
iPillage is a web application security testing tool designed to be lightweight and easy to use developed by dc414 for Chrome as a browser extension. Allowing anyone to pen-test any page they visit and all the links it might contain at the click of a button.
dc414 @ DEFCON19
ngharo and I will be giving a presentation at DEFCON19!! DefCon Groups asked us to talk a little about dc414. Like about how we run it, what we do at meetings, what we do in public, and other odds and ends. This will be a first and a honor for the both of us, It should be lots of fun 🙂
Know you rights event post…..blog post and news
The know your rights event was a huge success!! We took a bunch of pictures which we will be uploading later. I big thanks to Candlelight Collective, Waring R. Fincke, M.Peters Trucking, and the dc414 crew for making the event happen!!
And in other news, because most of us will be at DEFCON at the time our normal dc414 meeting takes place we will be moving the date to August 12th. Things will be back to normal in September.
June 2011 meeting recap
I know this post is a little late but we have been busy with other stuff, and my mom always said better late then never. Valdimir started us off with a fun demo of his magnetic card reader “vid below”, which could also write to a card but he didnt have the right software, he said he will be getting the right stuff soon. Then he came out with the big guns, a 3G/cell phone jammer!! This thing was all kinds of fun, and i uploaded a little vid of one of the demos we did with it “bellow”. The awesomeness didn’t end there, dw5304 gave us a nice demo of ZFS and showed off some of its more robust features. One of my personal favorite features was being able to pipe snap shots to anything!! Congrats to Darkwind for beeing last meetings winner of free junk from dc414!! Here are some pics taken at dc414.
Darkwind and his winnings!

Vlad reading cards:
Vlad be jammin:
More Blacklist
Got this email from the kind people at Demand Progress:
We’re forcing them to take our concerns seriously: Demand Progress members have sent more than 50,000 emails to Senators to urge them to oppose the Internet Blacklist Bill (the PROTECT IP Act). Now we’re hearing back from them, and one thing is clear: Our emails are compelling Senators to start thinking hard about Internet freedom.
PROTECT IP would give the government the power to force Internet service providers, search engines, and other “information location tools” to block users’ access to sites that have been accused of copyright infringement — the initiation of a China-style censorship regime here in the United States.
Will you email Congress to urge them to oppose the PROTECT IP Act? Just click here.
Senators are writing back to let us know that our emails are making them think twice before rubber-stamping PROTECT IP. For instance, Oregon’s Jeff Merkley is telling Demand Progress members:
I have heard from many Oregonians on both sides of this issue – those who support providing U.S. agencies with greater authority to shut down websites, and those who are worried that the legislation could result in Internet censorship. Thanks to your letter and the letters of fellow Oregonians, I have asked my staff to take a closer look into this legislation.
Thanks for fighting for Internet freedom!
Send a email to your senator now and stop this evil act.
Help 2600 Magazine Compile a List of Dates for their Hacker Calendar!
2600, the magazine familiar to many as a preeminent hacking quarterly, is publishing a calendar. While, according to the 2600 site, most calendars only mark holidays, 2600 intends to “provide as complete a guide to milestones in the hacker world as humanly possible.” Not an easy task considering that, depending on your definition, hacking could extend to the discovery of fire, or at least the wheel.
2600 gives some examples in which they only list events back to March 3, 1885, when AT&T was founded. If this example is followed, that “only” gives one 126 years to work with, but compiling a full list of hacking dates is still a daunting task. If you can think of any dates worthy of consideration, email them to: calendar@2600.com. We think maybe September 5th, 2004 might be a notable date to include. We’ll leave it up to figure out what that date is, in case it wasn’t painfully obvious.
OP: http://hackaday.com/2011/06/04/help-2600-magazine-compile-a-list-of-dates-for-their-hacker-calendar/
Defend Online Anonymity – Set Up a Tor Relay
Got this in a email from the good people over at EFF:
Dear Anarchy,
We use Tor to access our website and to publish to our blog, which is blocked inside of our country. — Iranian human rights activist
If you could do something to make the Internet safer and more private for activists, investigative journalists, and humanitarian aid workers around the world, would you?
You can.
Today EFF is launching the Tor Challenge—a campaign to encourage Internet users all over the world to support the Tor network by operating relays.
Tor is a service that helps you to protect your anonymity while using the Internet and allows you to circumvent Internet censorship. When you use the Tor software, your real IP address remains hidden. Activists all over the world depend on Tor to maintain anonymity when communicating and accessing websites that have been blocked by their governments.
The Tor software depends on the Tor network, which is made up of Tor relays operated by individuals like you. The more Tor relays we have running, the faster, more secure and more robust the Tor network becomes.
Are you ready to help Internet activists all over the world?
Click here to see how and learn more.
Defending your digital rights,
The EFF Activism Team
This is a great idea and more ppl should run tor exit relays, but it does not come with out some pains. I kept on getting DMCA notices so i had to employ a few exit policy rules on my relay. Here is the ones im using.
ExitPolicy accept *:20-23 # FTP, SSH, telnet
ExitPolicy accept *:43 # WHOIS
ExitPolicy accept *:53 # DNS
ExitPolicy accept *:79-81 # finger, HTTP
ExitPolicy accept *:88 # kerberos
ExitPolicy accept *:110 # POP3
ExitPolicy accept *:143 # IMAP
ExitPolicy accept *:194 # IRC
ExitPolicy accept *:220 # IMAP3
ExitPolicy accept *:443 # HTTPS
ExitPolicy accept *:464-465 # kpasswd, SMTP over SSL
ExitPolicy accept *:543-544
ExitPolicy accept *:563 # NNTP over SSL
ExitPolicy accept *:587 # SMTP
ExitPolicy accept *:706
ExitPolicy accept *:749 # kerberos
ExitPolicy accept *:873 # rsync
ExitPolicy accept *:902-904
ExitPolicy accept *:981
ExitPolicy accept *:989-995 # FTP over SSL, Netnews Administration System, telnets, IMAP over SSL, ircs, POP3 over SSL
ExitPolicy accept *:1194 # openvpn
ExitPolicy accept *:1220 # QT Server Admin
ExitPolicy accept *:1293 # PKT-KRB-IPSec
ExitPolicy accept *:1500 # VLSI License Manager
ExitPolicy accept *:1723 # PPTP
ExitPolicy accept *:1863 # MSNP
ExitPolicy accept *:2082-2083 # Radius
ExitPolicy accept *:2086-2087 # GNUnet, ELI
ExitPolicy accept *:2095-2096 # NBX
ExitPolicy accept *:3128 # SQUID
ExitPolicy accept *:3389 # MS WBT
ExitPolicy accept *:3690 # SVN
ExitPolicy accept *:4321 # RWHOIS
ExitPolicy accept *:4643
ExitPolicy accept *:5050 # MMCC
ExitPolicy accept *:5190 # ICQ
ExitPolicy accept *:5222-5223 # XMPP, XMPP over SSL
ExitPolicy accept *:5900 # VNC
ExitPolicy accept *:6666-6667 #IRC
ExitPolicy accept *:6679
ExitPolicy accept *:6697
ExitPolicy accept *:8000 # iRDMI
ExitPolicy accept *:8008
ExitPolicy accept *:8080 # HTTP Proxies
ExitPolicy accept *:8087-8088 # Simplify Media SPP Protocol, Radan HTTP
ExitPolicy accept *:8443 # PCsync HTTPS
ExitPolicy accept *:8888 # HTTP Proxies, NewsEDGE
ExitPolicy accept *:9418 # git
ExitPolicy accept *:9999 # distinct
ExitPolicy accept *:10000 # Network Data Management Protocol
ExitPolicy accept *:19638
ExitPolicy reject *:*
So anyway, yes everyone should run a tor relay and should also use the above for your tor relay config. On ubuntu boxes just search for ExitPolicy in /etc/tor/torrc and past it in. Be sure to comment out any pre-existing exit policies. Ok go set up a tor exit relay already!!
Know your rights event!!
dc414 is proud to produce the “Know your rights event” on July 1st 2011 at Candlelight Collective. The goal of this event is to educate the people and teach them how they can preserve their civil liberties during police encounters with confidence. The event will start with a viewing of the 40 minute film “10 Rules for Dealing with Police” from FlexYourRights.org followed by a few words from Waring R. Fincke attorney at law. After which there will be time for any questions the audience might have.
Help us spread the word! Download this flyer, make copies and post them around!
More info HERE
Cisco Small Business RV042 XSS
The RV042 is a Dual WAN, 4 port switch, VPN Router. Work just got it in to do a little load balancing and for fail over protection. One of my favorite things to do with new toys like this guy is give them a nice once over. Which of course is how i found a XSS in the login logging functions of this device. I was originally looking for weaknesses in the login scheme and notice that my attempts are being logged, notably the user name i was trying to login as was being logged, along with a brief description of the failure. I then put non-standard characters in there which broke the UI, after some more playing around i found i was able to get html to render, from there i just started messing with XSS payloads till i found one that worked.
Here is my working XSS at the login screen:
The string i used is < iframe src="https://new.dc414.org" >
For password i just put in some junk
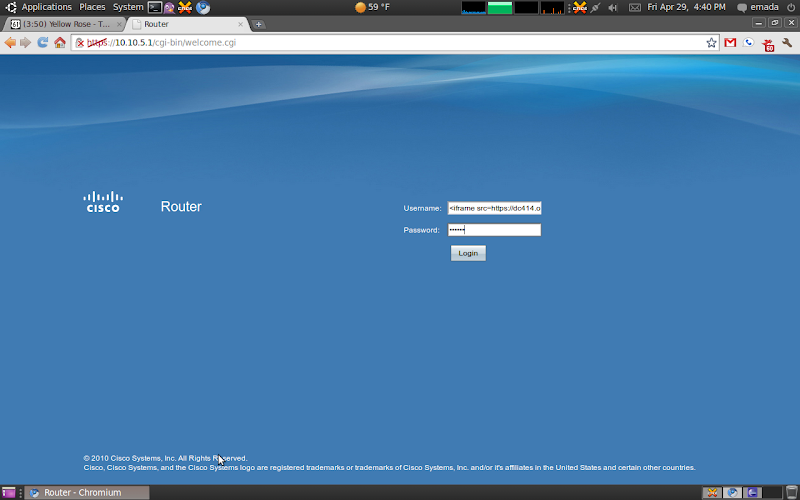
Here is what it looks like after i submit:

Here is the XSS in action 🙂

K thats it, enjoy, peace.
New meeting spot: Brewing Grounds for Change
We have switched places again, but i hope for the last time. The new venue is Brewing Grounds for Change on Farwell Avenue. For directions or more info check out the Meetings page. Another new thing we are starting is we are asking people that plan on coming to meetings to bring $5 or a non-perishable food item. The money will go toward paying for prizes “the ones we give away at meetings/events”, events and other stuff dc414. The food will go to the food pantry 🙂 We will see you at the next meeting!