The RV042 is a Dual WAN, 4 port switch, VPN Router. Work just got it in to do a little load balancing and for fail over protection. One of my favorite things to do with new toys like this guy is give them a nice once over. Which of course is how i found a XSS in the login logging functions of this device. I was originally looking for weaknesses in the login scheme and notice that my attempts are being logged, notably the user name i was trying to login as was being logged, along with a brief description of the failure. I then put non-standard characters in there which broke the UI, after some more playing around i found i was able to get html to render, from there i just started messing with XSS payloads till i found one that worked.
Here is my working XSS at the login screen:
The string i used is < iframe src="https://new.dc414.org" >
For password i just put in some junk
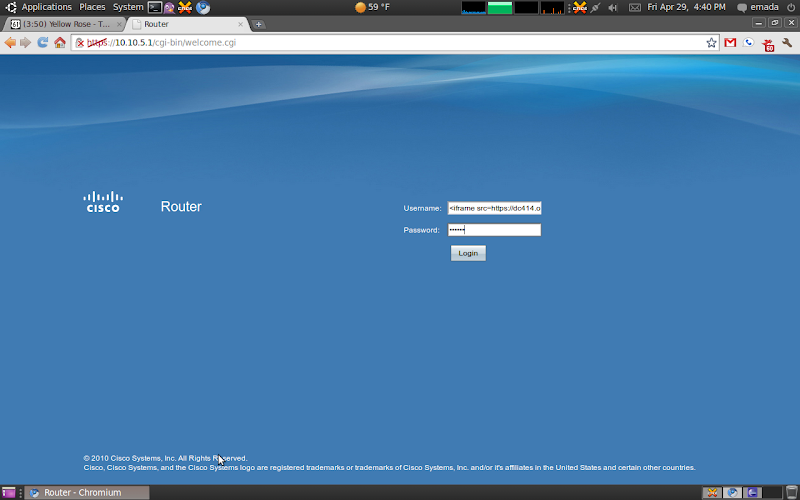
Here is what it looks like after i submit:

Here is the XSS in action 🙂

K thats it, enjoy, peace.






